Cyber-extortion: Trend and Case Studies
These attacks have also become more costly from year to year. In 2018, the average cost of a cyberattack to companies worldwide was USD 3.8 million (up from USD 3.6 million in 2017), while attacks cost US-based companies an average of USD 7.9 million (up from USD 7.3 million in 2017).
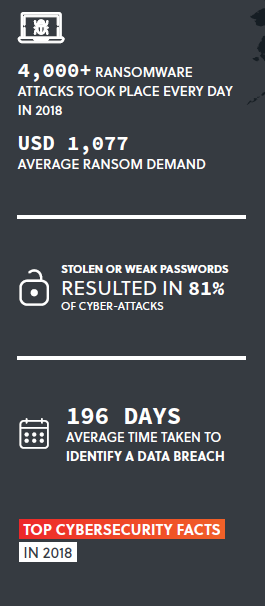
As well as the rising costs associated with cyber-attacks, there has been a general increase in the number of attacks targeting companies through business email compromise (BEC) incidents. The digital “spoofing” techniques, where hackers successfully imitate the email signatures of alleged senders, has intensified as a result of scams where attackers use deception to manipulate individuals into revealing personal and confidential information. These details are typically used to make emails which contain malware look more legitimate, with recipients then opening attachments and unknowingly installing crypto-miners or ransomware. Since January 2018, there has been a 350 percent increase in reported ransomware attacks globally, with more than half of all ransomware attacks targeting the healthcare industry. A wide range of actors perpetrated cyber-crimes in 2018, from hostile hacking groups to criminal organisations and state-sponsored actors. The United States’ Federal Bureau of Investigation (FBI) reported an increase in cyber-crimes perpetrated either exclusively by, or with the help of, state governments, allegedly including China, Russia, Iran and North Korea.
There has been a general increase in the number of attacks targeting companies through business email compromise (BEC) incidents.
Of particular concern for the cyber-security industry is that as the frequency of these attacks increased, there were fewer experienced cyber-security professionals available to help mitigate the impact of the attacks. This is because as companies become more technologically dependant, they concomitantly become more susceptible to attacks. This change is happening at a faster rate than cyber-security professionals with adequate experience are being trained. Given the continued digitalisation of key business operations, and the significant costs associated with being the victim of a cyber-attack, cyber-security is likely to remain a priority for individuals and companies alike in 2019.
Latin America (Mexico, Chile, Peru)
Several high-profile cyberattacks targeting financial institutions took place in the Latin America region in 2018, with notable examples in Mexico, Chile and Peru. In Mexico, the central bank, Banco de México, announced on 14 May 2018 that several institutions, including banks and stock exchanges, were attacked by hackers that targeted the software used to communicate with the SPEI, an intra-Mexico SWIFT-like protocol. An estimated MXN 400 million (USD 20.4 million) was transferred to fraudulent accounts before the Banco de México switched transfers to a more secure system. Similarly, in May, an unidentified perpetrator withdrew USD 10 million of company funds from the Banco de Chile after a targeted virus attack. Lastly in Peru, on 17 August 2018, a combination of ransomware, distributed denial-of-service (DDoS) attacks, and data-mining viruses attacked several financial bodies in the country, including banks, although the institutions were able to disconnect their systems and successfully counter any attempted theft or damage. This evidence suggests similar attacks can be expected in the coming year.
Middle East & North Africa (UAE)
In 2018, cyberextortion cases increased in the Middle East and North Africa region. According to Gulf Cooperation Council (GCC) officials, more than 50 percent of cyber extortion victims in the region, including the United Arab Emirates (UAE), are female social media users. The authorities found that many women fell victim to blackmail through the dissemination of personal data, especially photographs, on social media platforms. In 2017, Dubai police closed thousands of social media accounts involved in cyber-crimes and dismantled several gangs engaged in such practices. In 2018, Dubai and Abu Dhabi authorities introduced more stringent punishments for cybercrime. However, a comprehensive response to cybercrimes is prevented by victims’ decision to often not report such incidents as a result of the attached social stigma. Furthermore, the growing frequency of this form of cyber-extortion is related to increasingly advanced software programmes online with the ability to hack smartphones. People’s use of social media is also growing, increasing the risk of cyber extortion. As such, police in Abu Dhabi, for example, have warned against posting photos and videos on social media.
Asia Pacific (Australia)
In November 2018, Australian media reported that a local defence contractor specialising in shipbuilding had been the subject of a cyber-security breach and extortion attempt. The perpetrators reportedly accessed staff email addresses and phone numbers as well as ship drawings and designs. Some of that information was subsequently offered for sale on the dark web in what authorities described as an extortion attempt, with the hackers saying they would remove the information if an unconfirmed ransom amount was paid. Subsequent investigations traced the perpetrators to Iran. While the incident has raised considerable security concerns, particularly as the targeted company provides equipment to the US Navy, it is currently unclear if the hack was sanctioned by the Iranian government or carried out by criminals. Australian institutions, including companies and universities, have been increasingly targeted by Iran-based hackers in recent months as part of an ongoing attempt to steal intellectual property and academic research.
The perpetrators reportedly accessed staff email addresses and phone numbers as well as ship drawings and designs. Some of that information was subsequently offered for sale on the dark web.
Europe & North America (US)
In March 2018, two Iranian nationals perpetrated a large ransomware attack targeting the City of Atlanta, Georgia. At 05h20 local time on 22 March 2018, local authorities detected a ransomware attack targeting computers of all employees of the City of Atlanta, and received a ransom demand of USD 6,800 per infected device. The attack severely impacted day-to-day operations in the city, with customers unable to use customer-facing applications, including those used to pay bills and access court-related information. Three months after the attack, approximately a third of all software used by the City of Atlanta remained offline or partially disabled. During the course of the attack, the perpetrators received at least USD 6 million in ransom payments, while the City of Atlanta spent approximately USD 5 million on emergency information technology contracts to implement new cyber-security systems. The attack represented the largest successful cyber-security breach for a major US city by ransomware, with approximately six million people impacted by the incident.
